The scope of PCI DSS compliance is one of the most critical aspects of securing payment systems and protecting cardholder data. Proper scoping ensures organizations focus their efforts and resources on areas that directly interact with sensitive data, reducing vulnerabilities and maintaining compliance. This comprehensive guide delves into the components of scoping, including identifying Cardholder Data Environments (CDE), using segmentation techniques, managing third-party service provider involvement, and leveraging tools and technologies for scope reduction.
1. Identifying Cardholder Data Environments (CDE)
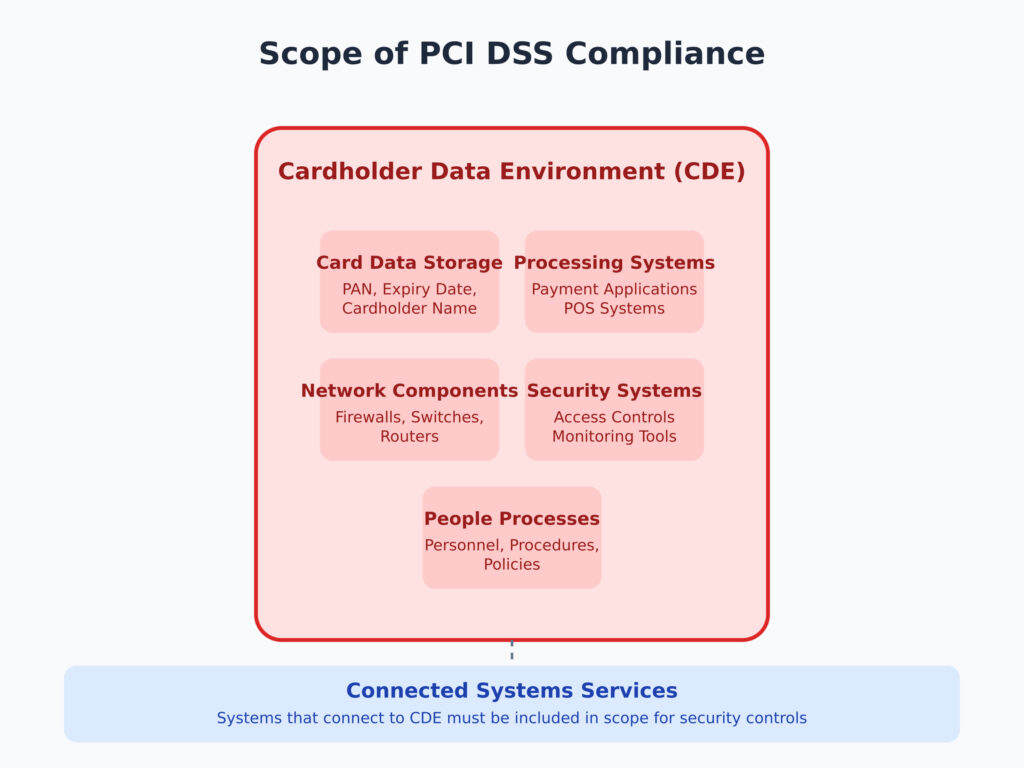
The Cardholder Data Environment (CDE) encompasses the systems, processes, people, and networks involved in storing, processing, or transmitting cardholder data or sensitive authentication data. Accurately identifying the CDE is the foundational step for scoping PCI DSS compliance.
Components of the CDE:
- Cardholder Data: This includes the Primary Account Number (PAN) and, if combined with the PAN, data such as the cardholder’s name, expiration date, and service code.
- Sensitive Authentication Data: Includes full track data from the magnetic stripe, CVV/CVC codes, and PINs, which must never be stored post-authorization.
Steps to Identify the CDE:
- Data Discovery:
Use automated tools to scan for PANs and other cardholder data across systems, databases, and devices. Ensure the discovery process covers all data sources, including backup files, email servers, and cloud environments. - Network Mapping:
Create detailed network diagrams showing how cardholder data flows within and between systems. Include all points of data entry, storage, processing, and transmission. - Connected Systems:
Identify any system or device that can interact with or affect the security of the CDE. Even systems that do not directly handle cardholder data but share a network or have administrative access are considered in scope.
By identifying the CDE accurately, organizations can better manage and secure their payment environments while minimizing unnecessary scope.
2. Scoping and Segmentation Techniques
Scoping defines the boundaries of PCI DSS compliance, while segmentation is a method of isolating the CDE from non-CDE systems to reduce the compliance footprint. These techniques are essential for efficient and effective PCI DSS implementation.
Understanding Scoping:
Scoping includes all systems, devices, and processes that store, process, or transmit cardholder data and those that can impact the security of the CDE. This includes:
- POS systems, payment gateways, and databases handling cardholder data.
- Supporting systems like DNS, NTP servers, and logging systems that interact with the CDE.
- Systems with administrative access to the CDE.
Segmentation for Scope Reduction:
Segmentation isolates the CDE from non-CDE systems, reducing the number of systems within scope for PCI DSS.
- Techniques:
- Implement firewalls to restrict traffic between the CDE and other systems.
- Use Access Control Lists (ACLs) to define which systems can communicate with the CDE.
- Deploy Virtual Local Area Networks (VLANs) to segregate network traffic.
- Validation: Regularly test segmentation controls to confirm their effectiveness. A penetration test should verify that non-CDE systems cannot access cardholder data or impact the CDE’s security.
Effective segmentation reduces compliance costs and simplifies ongoing management by limiting the scope to essential systems.
3. Third-Party Service Provider Involvement
Third-party service providers (TPSPs) play a critical role in the payment ecosystem, offering services such as payment processing, cloud hosting, and data storage. Because TPSPs often have access to cardholder data or systems within scope, their involvement must be carefully managed.
Roles and Responsibilities:
- Service Provider Accountability:
TPSPs must comply with PCI DSS requirements relevant to their services. This includes implementing appropriate security controls and demonstrating compliance through audits and assessments. - Shared Responsibility Model:
Organizations and TPSPs share responsibility for PCI DSS compliance. For example:- The organization might be responsible for securing its internal network.
- The TPSP may handle encryption during payment processing.
Managing Third-Party Relationships:
- Contracts and Agreements:
- Ensure that contracts explicitly define the TPSP’s PCI DSS responsibilities.
- Include clauses for regular compliance validation and incident reporting.
- Due Diligence:
- Evaluate the provider’s security practices, including their compliance status, before engagement.
- Request evidence of compliance, such as an Attestation of Compliance (AOC) or Report on Compliance (ROC).
- Monitoring and Auditing:
- Regularly review the TPSP’s compliance status through audits or certifications.
- Implement processes for continuous monitoring of their services to identify potential risks.
Organizations must understand that even when outsourcing services, they retain ultimate responsibility for ensuring PCI DSS compliance.
4. Tools and Technologies for Scope Reduction
Tools and technologies play a vital role in minimizing the scope of PCI DSS compliance, enhancing security while reducing the complexity of securing a broad environment.
Key Tools and Technologies:
- Tokenization:
- Replaces sensitive cardholder data with unique tokens that have no exploitable value.
- Systems storing tokens instead of raw cardholder data can often be excluded from PCI DSS scope.
- Example: A POS system processes tokens rather than actual card data, reducing its compliance footprint.
- Point-to-Point Encryption (P2PE):
- Encrypts cardholder data at the point of entry (e.g., POS terminals) and decrypts it only at a secure endpoint.
- Protects data during transmission, ensuring that intermediate systems remain out of scope.
- Cloud-Based Payment Solutions:
- Outsource cardholder data handling to a secure, PCI DSS-compliant cloud provider.
- Limits in-scope systems to those necessary for business operations.
- Firewall and Segmentation Tools:
- Use advanced firewalls to enforce strict network segmentation.
- Monitor and log traffic between segmented environments to ensure no unauthorized access occurs.
- Data Discovery and Classification Tools:
- Automate the identification of cardholder data across systems.
- Classify data based on its sensitivity to enforce proper storage and access policies.
- Identity and Access Management (IAM):
- Control who can access cardholder data with multi-factor authentication (MFA) and role-based access controls (RBAC).
Benefits of Scope Reduction:
- Reduces the time, effort, and cost of PCI DSS compliance.
- Minimizes the risk of data breaches by limiting the exposure of sensitive data.
- Simplifies the implementation and validation of security controls.
Key Considerations for Effective Scoping
- Regular Scope Review:
- Periodically reassess the CDE and related systems to account for changes in business processes, technology, or infrastructure.
- Employee Training:
- Educate employees about the importance of PCI DSS compliance and their role in maintaining secure environments.
- Documentation:
- Maintain detailed documentation of scope boundaries, segmentation controls, and third-party agreements to demonstrate compliance during audits.
Conclusion
Understanding and managing the scope of PCI DSS compliance is critical for securing payment systems and protecting cardholder data. By accurately identifying the CDE, employing segmentation techniques, managing third-party relationships, and leveraging tools for scope reduction, organizations can streamline compliance efforts while enhancing security. A well-managed scope ensures not only regulatory compliance but also a robust defense against evolving cyber threats.
To read Module 4: Risk Management and Vulnerability Assessments
