The PCI DSS framework consists of 12 comprehensive requirements aimed at securing payment card data. These requirements are divided into six categories that ensure organizations build a secure environment, protect cardholder data, and maintain robust security policies. This tutorial provides a detailed exploration of each requirement to help organizations achieve compliance and secure their payment systems effectively.
1. Install and Maintain a Firewall Configuration
A firewall is the first line of defense in securing a network. It acts as a barrier between trusted internal networks and untrusted external networks, such as the internet.
- Objective: To block unauthorized access to systems that store, process, or transmit cardholder data.
- Best Practices:
- Implement and regularly update firewall rules to allow only necessary traffic.
- Document and review firewall configurations periodically.
- Restrict access to systems based on specific IP addresses and ports.
A well-maintained firewall configuration reduces the risk of data breaches caused by external threats.
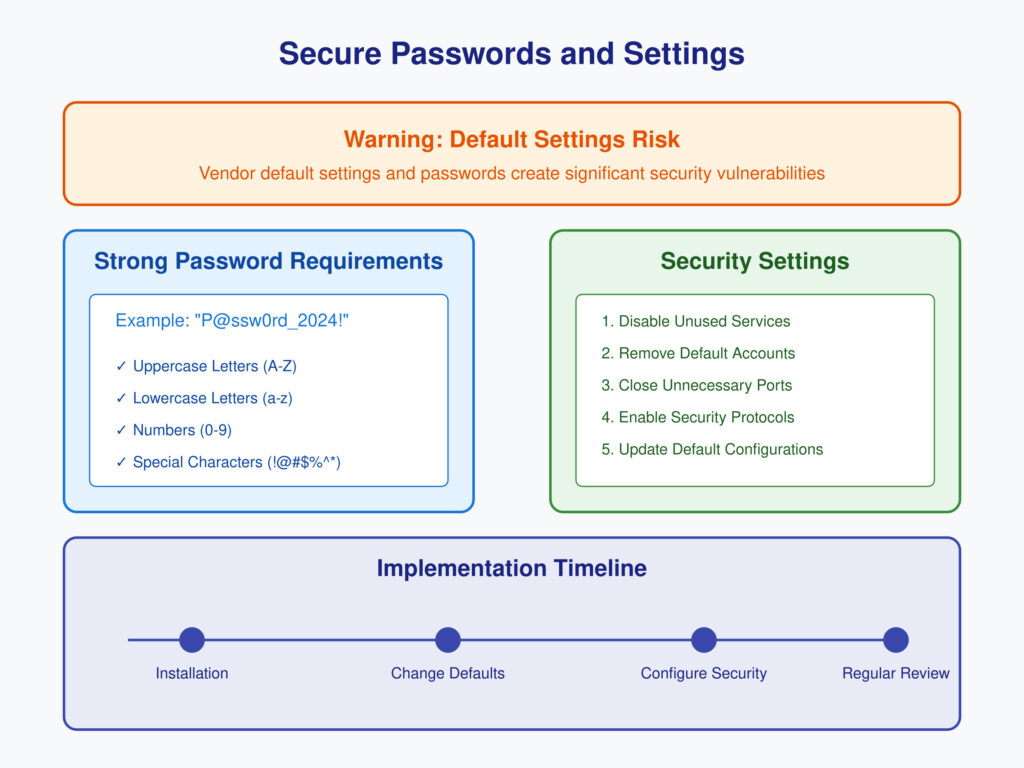
2. Use Secure Passwords and Settings
Default settings and passwords provided by vendors often lack robust security, making systems vulnerable.
- Objective: Replace default credentials and settings with secure configurations to prevent unauthorized access.
- Implementation Tips:
- Use strong, unique passwords that combine upper and lowercase letters, numbers, and symbols.
- Disable unnecessary services and protocols in devices.
- Change default passwords immediately upon installation of hardware or software.
Ensuring secure passwords and configurations is a critical step in protecting sensitive systems from brute force and other attacks.
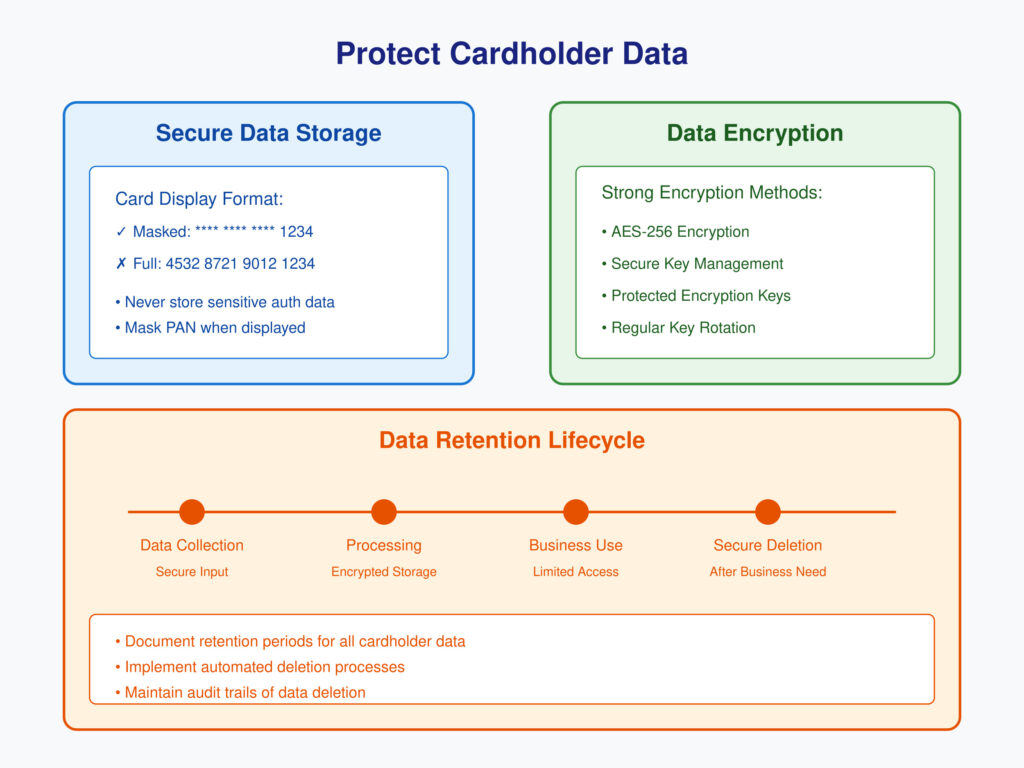
3. Protect Cardholder Data
Cardholder data must be protected during both storage and transmission to prevent unauthorized disclosure.
- Key Components:
- Storage: Mask sensitive authentication data (e.g., PINs or full card numbers) when displaying it. Only the last four digits should be visible.
- Encryption: Encrypt stored cardholder data using strong algorithms, such as AES-256.
- Retention Policy: Retain cardholder data only for as long as it is necessary for business purposes and securely delete it afterward.
Protecting cardholder data ensures compliance and safeguards customer trust.
4. Encrypt Transmission of Data Across Public Networks
Data transmitted over public or untrusted networks is susceptible to interception and theft. Encryption ensures that even if intercepted, the data remains unreadable.
- Implementation Guidelines:
- Use secure protocols such as TLS 1.2 or higher for encrypting data in transit.
- Avoid using outdated protocols like SSL and early versions of TLS.
- Regularly test encryption configurations to ensure they meet security standards.
Encryption protects sensitive data from eavesdropping and man-in-the-middle attacks.
5. Use and Regularly Update Anti-Virus Software
Malware poses a significant threat to the security of systems handling payment card data. Anti-virus software helps mitigate this risk.
- Best Practices:
- Deploy anti-virus software on all systems that are prone to malware infections.
- Configure automatic updates for anti-virus definitions to ensure protection against emerging threats.
- Regularly perform scans and monitor logs for suspicious activity.
A proactive approach to malware protection significantly reduces the risk of data breaches.
6. Develop and Maintain Secure Systems and Applications
Vulnerabilities in software and systems are often exploited by attackers to gain unauthorized access.
- Security Measures:
- Apply security patches promptly to address known vulnerabilities.
- Use secure coding practices during application development.
- Conduct regular vulnerability assessments to identify and fix security gaps.
Keeping systems and applications secure is an ongoing process that requires constant vigilance.
7. Restrict Access to Cardholder Data by Business Need-to-Know
Access to cardholder data should be granted only to those who need it to perform their job functions.
- Key Strategies:
- Implement role-based access controls (RBAC) to limit access based on roles and responsibilities.
- Review access rights regularly to ensure they align with current job roles.
- Use data masking to minimize exposure of sensitive information to unauthorized personnel.
Restricting access reduces the risk of insider threats and data misuse.
8. Identify and Authenticate Access to Systems
Strong identification and authentication mechanisms ensure that only authorized users can access systems.
- Recommendations:
- Use unique IDs for each user to track activity accurately.
- Implement multi-factor authentication (MFA) for systems that handle sensitive data.
- Enforce account lockout policies after multiple failed login attempts.
Authentication measures are vital for accountability and security.
9. Restrict Physical Access to Cardholder Data
Physical security is as important as digital security in protecting cardholder data.
- Best Practices:
- Store cardholder data in secure locations with restricted access.
- Use access controls such as key cards, biometric scanners, or PIN codes for data centers.
- Maintain visitor logs and monitor physical access through surveillance systems.
Physical restrictions safeguard data against unauthorized access or theft.
10. Track and Monitor Access to Network Resources and Cardholder Data
Logging and monitoring activities provide insights into who accessed what, when, and how.
- Implementation Tips:
- Enable logging for all access to cardholder data and critical systems.
- Regularly review logs to detect anomalies or unauthorized activity.
- Use automated tools to correlate logs and alert administrators of suspicious behavior.
Monitoring access ensures transparency and helps detect potential threats early.
11. Regularly Test Security Systems and Processes
Testing security systems proactively identifies vulnerabilities and ensures compliance with PCI DSS.
- Testing Requirements:
- Perform quarterly vulnerability scans using approved scanning vendors (ASVs).
- Conduct annual penetration tests to simulate real-world attack scenarios.
- Review and update testing procedures as systems evolve.
Regular testing builds resilience against cyberattacks.
12. Maintain a Policy Addressing Information Security
A robust information security policy provides a foundation for implementing and maintaining PCI DSS controls.
- Policy Essentials:
- Clearly define security roles and responsibilities within the organization.
- Include guidelines for employee training, risk assessments, and incident response.
- Review and update the policy regularly to address emerging threats and changes in business processes.
A well-defined policy ensures consistent and effective security practices across the organization.
Conclusion
The 12 PCI DSS requirements provide a comprehensive framework to secure cardholder data and protect payment systems. By implementing these measures, organizations can not only achieve compliance but also build a robust defense against evolving security threats. Compliance with PCI DSS is not just a regulatory necessity—it is a commitment to safeguarding customer trust and maintaining a secure payment ecosystem.
For reading Module 3: Scope of PCI DSS Compliance
