Compliance validation and reporting are critical components of PCI DSS, ensuring organizations maintain adherence to security standards and demonstrate their commitment to protecting cardholder data. This module focuses on the roles and responsibilities of key stakeholders, the use of Self-Assessment Questionnaires (SAQs), preparation for PCI DSS audits, and implementing compliance monitoring and remediation plans.
1. Roles and Responsibilities (QSA, ISA, and Merchants)
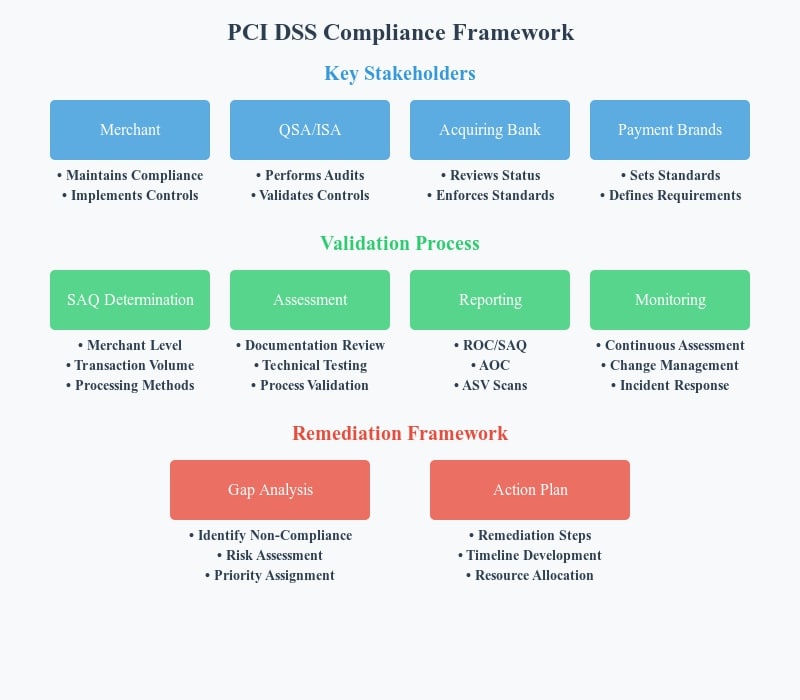
PCI DSS compliance involves multiple stakeholders, each playing a distinct role in achieving and validating compliance. Understanding these roles is crucial for ensuring successful implementation and ongoing adherence to PCI DSS requirements.
Qualified Security Assessor (QSA)
- Role:
QSAs are independent security professionals certified by the PCI Security Standards Council (PCI SSC) to assess an organization’s compliance with PCI DSS. - Responsibilities:
- Conduct on-site assessments for merchants and service providers.
- Review and validate the organization’s security controls against PCI DSS requirements.
- Provide a Report on Compliance (ROC) summarizing findings and recommendations.
- Offer expert guidance on achieving and maintaining compliance.
Internal Security Assessor (ISA)
- Role:
ISAs are employees within an organization who have completed PCI SSC-approved training to assess and validate internal compliance. - Responsibilities:
- Perform internal assessments to ensure PCI DSS adherence.
- Act as a liaison between the organization and external QSAs.
- Support compliance initiatives by providing expertise on PCI DSS requirements.
- Advantages:
- ISAs provide cost-effective assessments for organizations with a strong internal security team.
Merchants
- Role:
Merchants are businesses that process, store, or transmit cardholder data and must comply with PCI DSS based on their transaction volume and type. - Responsibilities:
- Determine their compliance level (e.g., Level 1 to Level 4) based on transaction volume.
- Complete the appropriate validation process, such as SAQs or ROC.
- Implement security controls to meet PCI DSS requirements.
2. Self-Assessment Questionnaires (SAQs)
SAQs are tools designed to help merchants and service providers evaluate their compliance with PCI DSS. They provide a structured approach for identifying gaps and documenting adherence to security standards.
Types of SAQs
There are multiple types of SAQs, each tailored to specific business scenarios:
- SAQ A:
- For merchants who outsource all cardholder data processing to third-party service providers.
- Minimal PCI DSS requirements apply since no cardholder data is stored or processed internally.
- SAQ B:
- For merchants using standalone dial-up terminals with no internet connectivity.
- SAQ C:
- For merchants with payment applications connected to the internet but with a segmented cardholder data environment.
- SAQ D:
- For merchants and service providers handling cardholder data in complex environments.
- Covers all PCI DSS requirements and is the most comprehensive SAQ.
- SAQ P2PE:
- For merchants using PCI-approved point-to-point encryption (P2PE) solutions.
Steps for Completing SAQs
- Identify the Applicable SAQ:
- Determine which SAQ applies to the organization based on its payment environment.
- Review PCI DSS Requirements:
- Familiarize the team with the requirements outlined in the SAQ.
- Evaluate Compliance:
- Answer each question honestly, identifying areas of non-compliance.
- Document Findings:
- Provide evidence to support compliance with each requirement.
- Remediate Gaps:
- Address non-compliant areas before submitting the SAQ.
- Submit to Acquirer or Payment Brand:
- Share the completed SAQ with relevant stakeholders as part of the compliance validation process.
3. Preparing for PCI DSS Audits
Audits are a key component of compliance validation, especially for organizations requiring on-site assessments by a QSA. Preparation is critical for ensuring a smooth and successful audit process.
Steps for Audit Preparation
- Understand Audit Scope:
- Clearly define the systems, processes, and environments that fall under the Cardholder Data Environment (CDE).
- Include all components that store, process, or transmit cardholder data.
- Gather Documentation:
- Compile necessary documentation, such as network diagrams, access control policies, and vulnerability scan reports.
- Ensure logs and records are organized and readily available for review.
- Conduct Internal Assessments:
- Perform a thorough internal review to identify and remediate gaps before the formal audit.
- Use tools such as vulnerability scanners and penetration testing to validate security controls.
- Engage Stakeholders:
- Involve key personnel from IT, security, and operations teams to provide necessary input and support during the audit.
- Review Policies and Procedures:
- Ensure all policies and procedures are up to date and aligned with PCI DSS requirements.
- Simulate the Audit Process:
- Conduct mock audits to familiarize the team with the process and address potential challenges.
Benefits of Audit Preparation:
- Minimizes surprises during the audit process.
- Demonstrates a proactive approach to compliance.
- Enhances the organization’s ability to address auditor questions effectively.
4. Compliance Monitoring and Remediation Plans
Compliance is not a one-time activity but an ongoing process that requires continuous monitoring and timely remediation of issues.
Compliance Monitoring
- Regular Assessments:
- Conduct periodic reviews to ensure ongoing adherence to PCI DSS requirements.
- Use automated tools to monitor system configurations, access controls, and network activity.
- Vulnerability Management:
- Perform quarterly vulnerability scans and penetration tests.
- Address identified vulnerabilities promptly to reduce risk.
- Log Monitoring and Analysis:
- Use Security Information and Event Management (SIEM) systems to analyze logs for anomalies.
- Set up alerts for suspicious activities, such as unauthorized access attempts or unusual traffic patterns.
- Policy Reviews:
- Update security policies and procedures regularly to reflect changes in the payment environment or regulatory requirements.
Remediation Plans
- Identify Non-Compliance Issues:
- Use SAQs, audits, and monitoring tools to identify areas where the organization falls short of PCI DSS requirements.
- Develop a Remediation Roadmap:
- Prioritize issues based on their risk level and potential impact on cardholder data security.
- Allocate resources and set deadlines for addressing high-priority issues.
- Implement Changes:
- Deploy technical, administrative, and physical controls to remediate identified gaps.
- Test changes to ensure they effectively address compliance requirements.
- Validate Improvements:
- Conduct follow-up assessments to confirm that remediation efforts have been successful.
- Document changes and update compliance records accordingly.
Conclusion
Compliance validation and reporting are essential components of maintaining PCI DSS adherence and protecting sensitive cardholder data. By understanding the roles of QSAs, ISAs, and merchants, utilizing SAQs effectively, preparing thoroughly for audits, and implementing robust monitoring and remediation plans, organizations can ensure continuous compliance and a secure payment environment. A proactive approach to these processes not only reduces the risk of data breaches but also builds trust with customers and stakeholders in an increasingly security-conscious world.
