Implementing and maintaining PCI DSS compliance is a continuous process that requires organizations to establish secure systems, implement robust controls, and actively monitor their environments. This module provides a detailed understanding of the critical components involved, including building secure network systems, data encryption methods and key management, access control mechanisms, logging and monitoring activities, and incident response procedures.
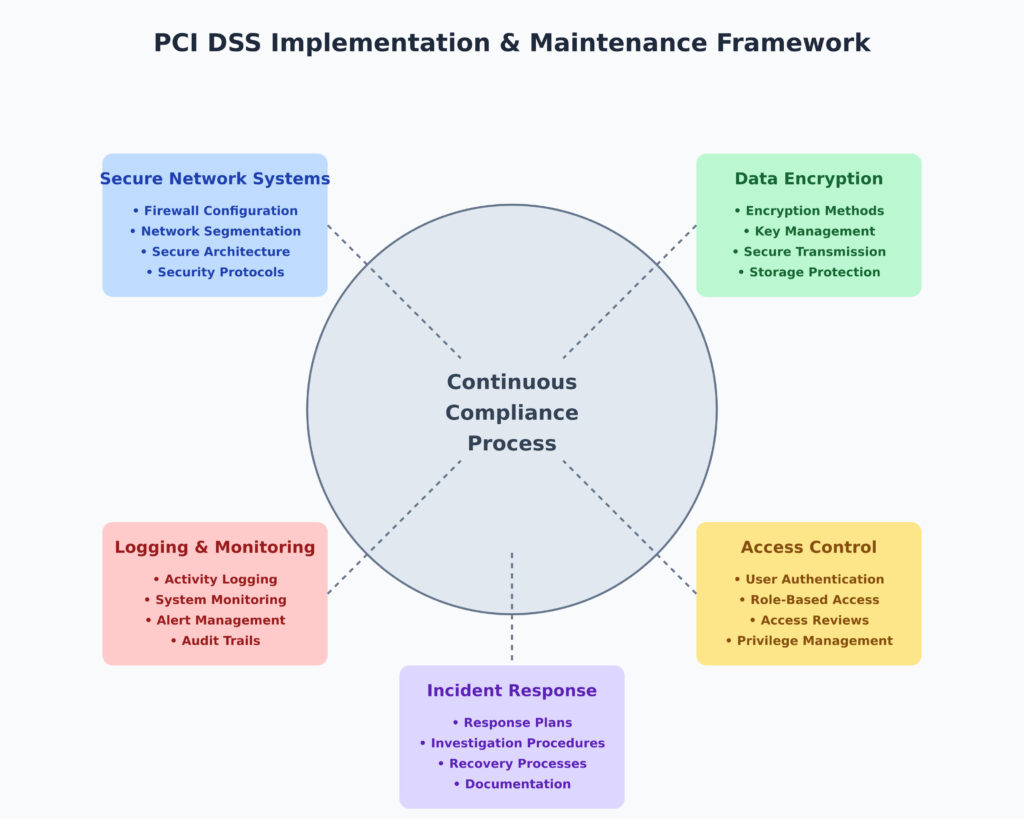
1. Building Secure Network Systems
A secure network forms the backbone of PCI DSS compliance. Payment environments must be designed to protect cardholder data from internal and external threats.
Key Considerations for Secure Networks:
- Firewall Configuration:
- Firewalls are the first line of defense against unauthorized access.
- Deploy firewalls at the perimeter and within internal networks to isolate the Cardholder Data Environment (CDE).
- Configure rules to restrict access based on business need, blocking all unnecessary traffic by default.
- Network Segmentation:
- Separate the CDE from other parts of the network using segmentation techniques such as VLANs or subnets.
- Proper segmentation reduces the scope of PCI DSS compliance and limits the impact of a potential breach.
- Secure Communication Channels:
- Use secure protocols such as HTTPS, TLS, or IPSec for transmitting data.
- Ensure all wireless networks are encrypted with strong algorithms (e.g., WPA3).
- Regular Updates:
- Keep network devices such as routers, switches, and firewalls updated with the latest firmware and security patches.
2. Data Encryption Methods and Key Management
Encryption is a cornerstone of protecting sensitive cardholder data. Proper encryption ensures that even if data is intercepted, it cannot be read or misused.
Data Encryption Methods:
- End-to-End Encryption (E2EE):
- Encrypts data from the point of capture (e.g., POS terminal) to its final destination (e.g., payment processor).
- Prevents data exposure during transmission.
- Tokenization:
- Replaces cardholder data with non-sensitive tokens, reducing the risk of exposure.
- Tokens are meaningless outside the specific system and can be stored without being subject to PCI DSS requirements.
- Storage Encryption:
- Encrypt stored cardholder data using strong algorithms such as AES-256.
- Ensure encryption keys are securely stored and rotated periodically.
Key Management:
- Key Creation and Distribution:
- Generate keys using secure methods and distribute them only to authorized individuals or systems.
- Key Storage:
- Store encryption keys in hardware security modules (HSMs) or secure key management systems to prevent unauthorized access.
- Key Rotation:
- Rotate keys regularly and immediately after suspected compromise.
- Access Control:
- Limit access to encryption keys based on the principle of least privilege.
Proper encryption and key management protect cardholder data throughout its lifecycle, meeting PCI DSS requirements and reducing exposure to risk.
3. Access Control Mechanisms
Access control mechanisms ensure that only authorized individuals can access systems and data within the CDE. Strong access controls are a critical requirement of PCI DSS.
Principles of Access Control:
- Least Privilege:
- Grant access to systems and data only to users who need it to perform their job functions.
- Regularly review access permissions and revoke unnecessary privileges.
- Role-Based Access Control (RBAC):
- Assign access rights based on predefined roles, ensuring consistency and reducing the risk of over-provisioning.
- Multi-Factor Authentication (MFA):
- Implement MFA for access to critical systems and administrative accounts.
- Use a combination of factors such as passwords, smart cards, and biometrics.
- Unique User IDs:
- Assign unique IDs to all users to ensure accountability and traceability.
- Avoid the use of shared or generic accounts.
Secure Password Practices:
- Enforce strong password policies, including complexity requirements and regular expiration.
- Prohibit the reuse of passwords and educate users on safe password practices.
4. Logging and Monitoring Activities
Effective logging and monitoring are crucial for detecting suspicious activity, investigating incidents, and maintaining PCI DSS compliance.
Key Logging Requirements:
- Comprehensive Logs:
- Capture logs for all access to systems, applications, and cardholder data.
- Include details such as user ID, timestamp, activity performed, and system affected.
- Secure Log Storage:
- Protect logs from unauthorized access, alteration, or deletion.
- Retain logs for at least one year, with immediate access to the last three months.
Monitoring Activities:
- Real-Time Monitoring:
- Use Security Information and Event Management (SIEM) systems to monitor and analyze logs in real-time.
- Set up alerts for critical events such as failed login attempts, unauthorized access, or unusual traffic patterns.
- Regular Log Reviews:
- Review logs daily to identify anomalies and security incidents.
- Document findings and take corrective actions when necessary.
- Incident Investigation:
- Use logs to trace the source of security incidents and determine their scope and impact.
Logging and monitoring provide visibility into the payment environment, enabling proactive threat detection and response.
5. Incident Response Procedures
An effective incident response plan is essential for addressing security breaches and minimizing their impact. PCI DSS requires organizations to have documented and tested incident response procedures.
Components of an Incident Response Plan:
- Preparation:
- Identify roles and responsibilities for the incident response team.
- Establish communication channels and escalation paths.
- Ensure access to necessary tools and resources, such as forensic software and contact lists for third-party experts.
- Detection and Analysis:
- Monitor systems and logs to detect potential incidents.
- Analyze alerts and logs to confirm the nature and severity of the incident.
- Containment:
- Isolate affected systems to prevent the spread of the incident.
- Implement temporary measures to secure the environment while preserving evidence for investigation.
- Eradication:
- Identify and eliminate the root cause of the incident, such as malware or unauthorized access.
- Apply patches and updates to prevent recurrence.
- Recovery:
- Restore systems to normal operations, ensuring that they are secure and fully functional.
- Validate that no residual vulnerabilities or threats remain.
- Post-Incident Review:
- Conduct a thorough review of the incident to identify lessons learned.
- Update the incident response plan and security controls based on findings.
Testing the Plan:
- Conduct regular tabletop exercises and simulated attacks to test the plan’s effectiveness.
- Involve all relevant stakeholders and refine procedures based on test results.
Conclusion
Implementing and maintaining PCI DSS compliance requires a holistic approach that integrates secure network design, robust encryption and key management, effective access controls, proactive logging and monitoring, and well-defined incident response procedures. By adopting these best practices, organizations can protect sensitive cardholder data, meet regulatory requirements, and strengthen their overall security posture. Continuous vigilance, regular testing, and ongoing improvement are essential for staying ahead of evolving threats and ensuring compliance in the dynamic payment environment.
